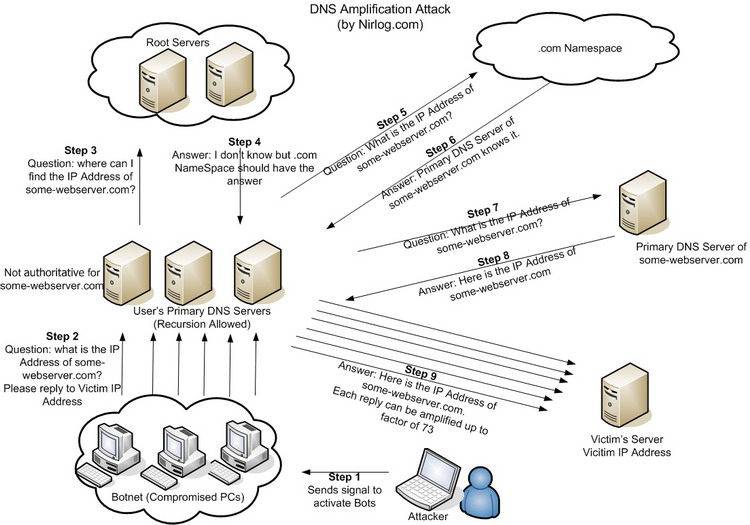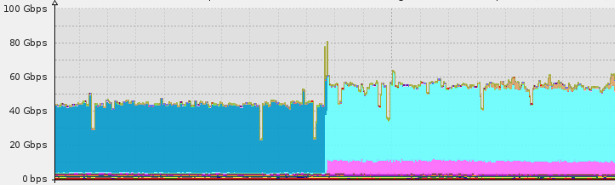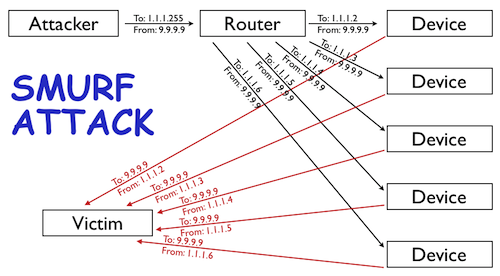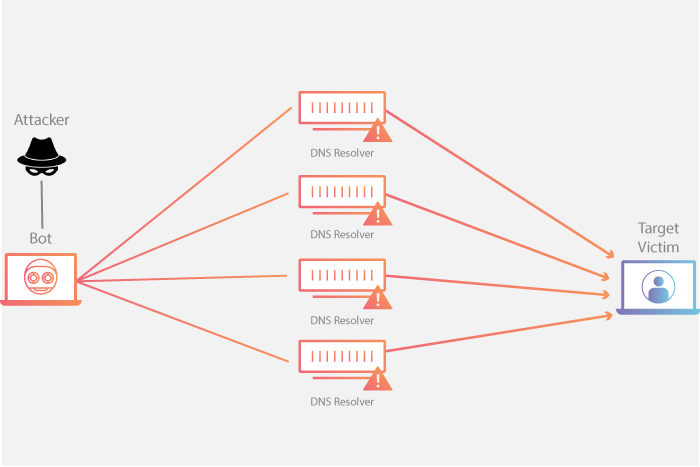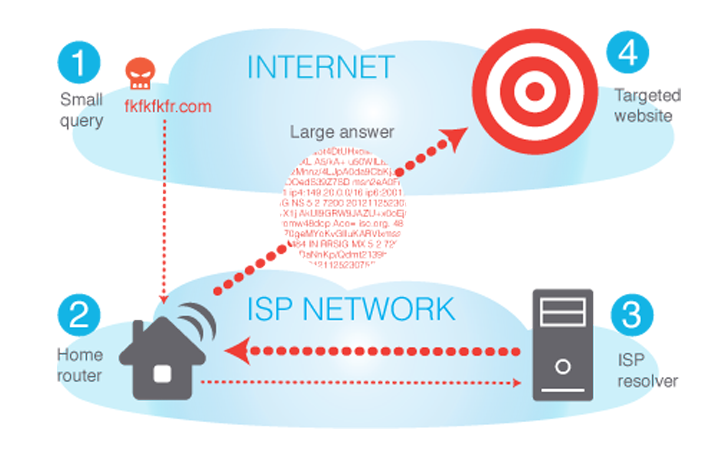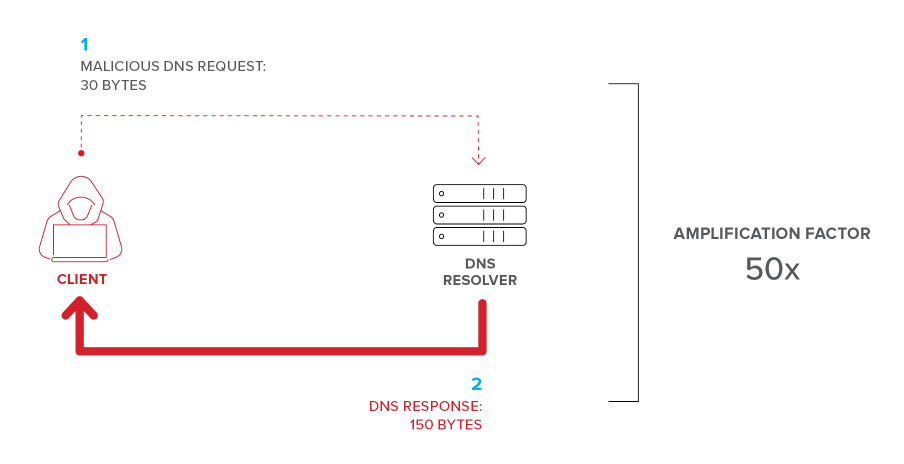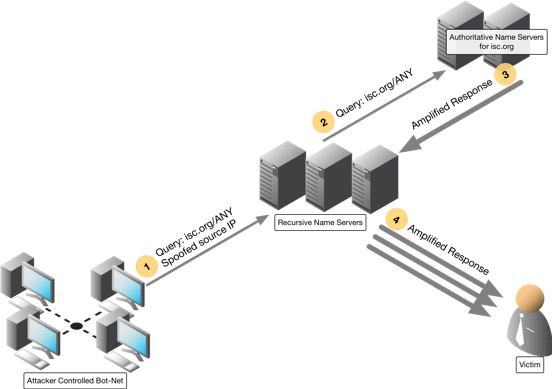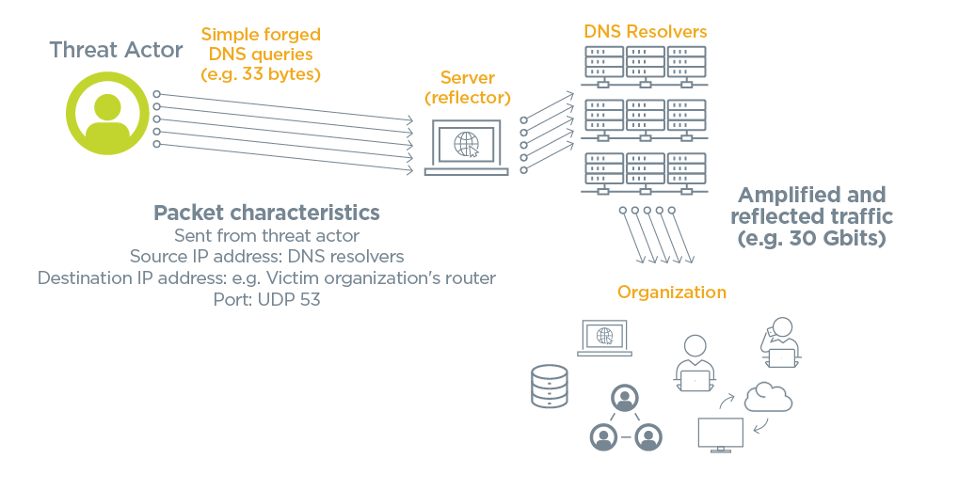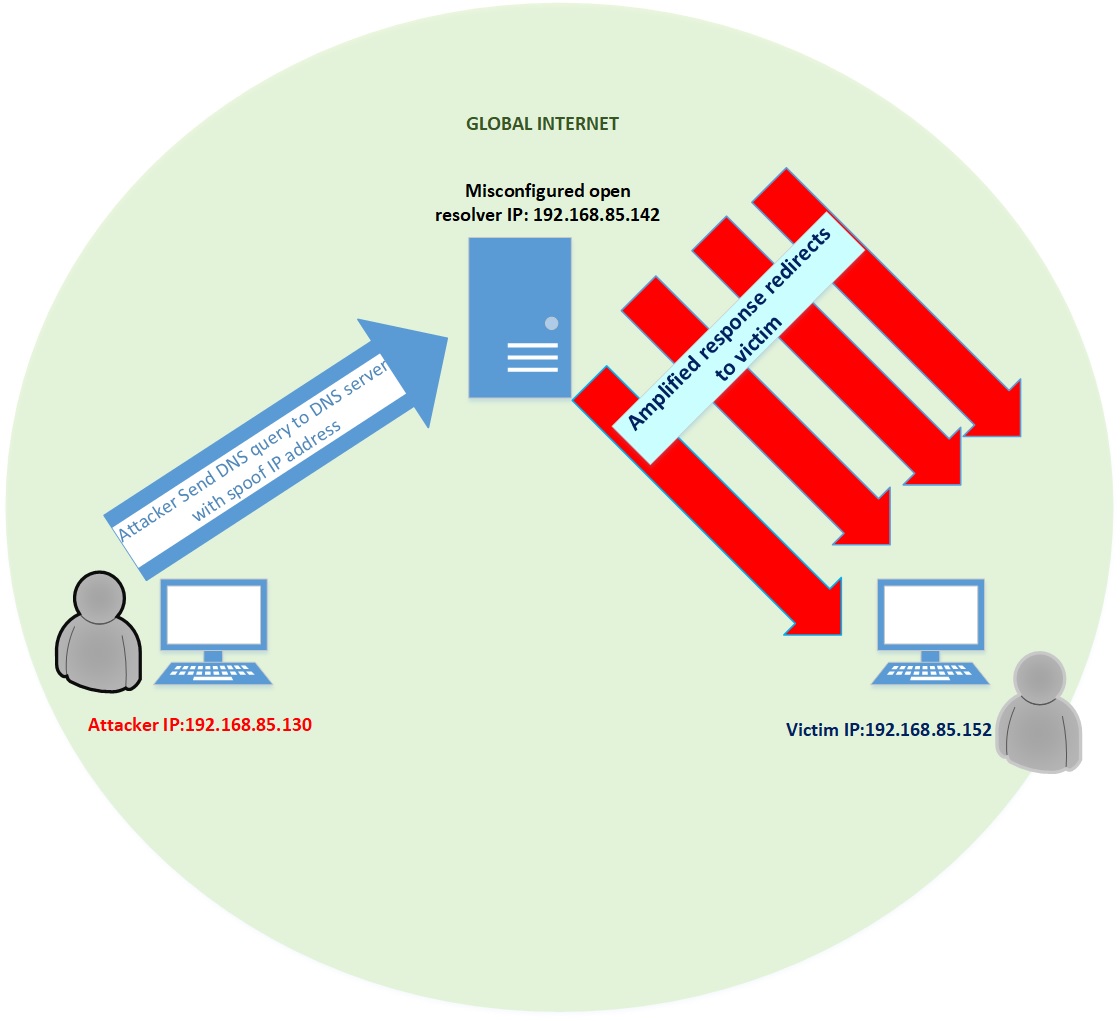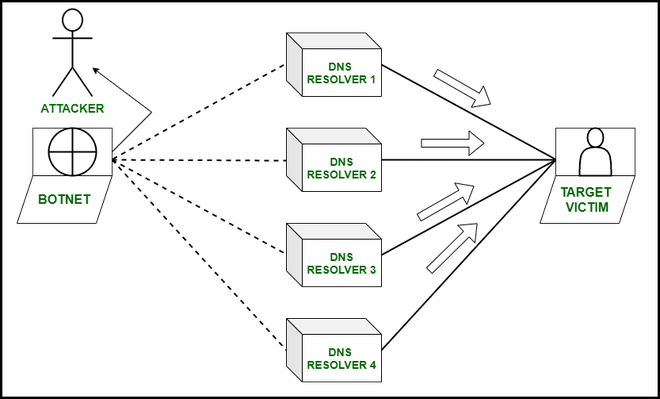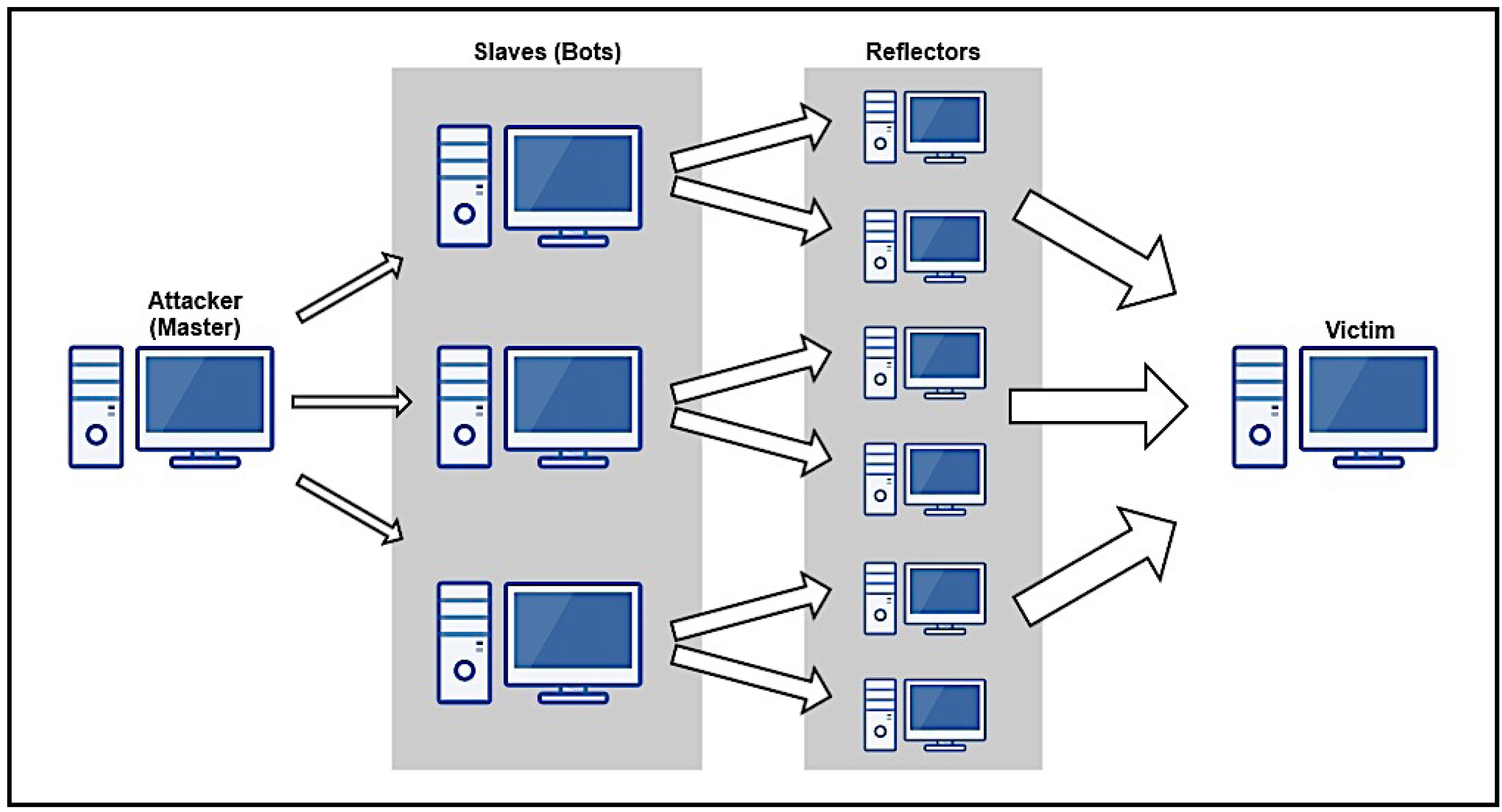
Sensors | Free Full-Text | A Methodological Approach for Assessing Amplified Reflection Distributed Denial of Service on the Internet of Things
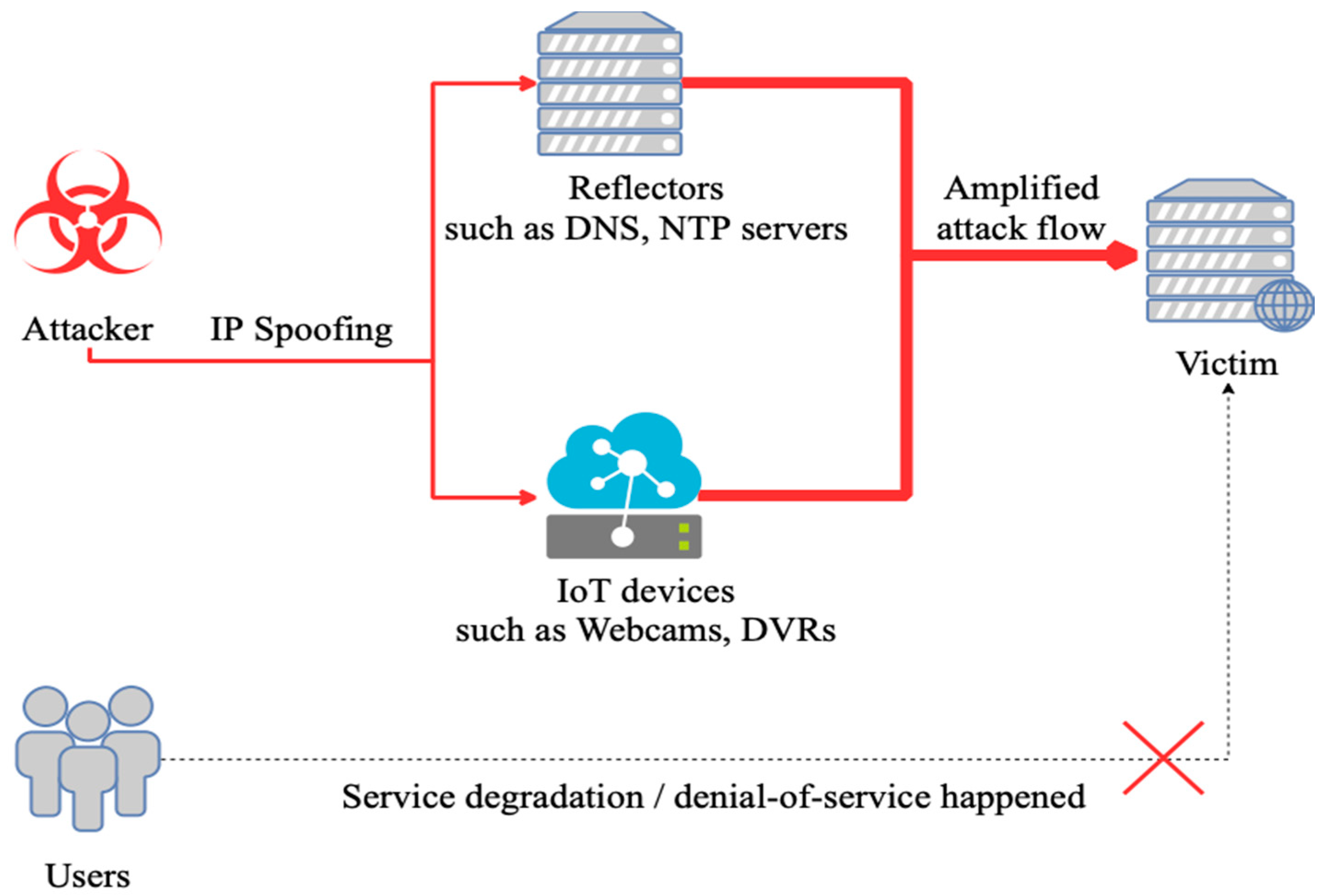
Symmetry | Free Full-Text | A DRDoS Detection and Defense Method Based on Deep Forest in the Big Data Environment